Microsoft addressed our LocalPotato vulnerability in the SMB scenario with CVE-2023-21746 during the January 2023 Patch Tuesday. However, the HTTP scenario remains unpatched, as per Microsoft’s decision, and it is still effective on updated systems.
This is clearly an edge case, but it is important to be aware of it and avoid situations that could leave you vulnerable.
In this brief post, we will explain a possible method of performing an arbitrary file write with SYSTEM privileges starting from a standard user by leveraging the context swap in HTTP NTLM local authentication using the WEBDAV protocol.
For all the details about the NTLM Context swapping refer to our previous post.
Lab setup
First of all, we need to install IIS on our Windows machine and enable Webbav, The following screenshot is taken from Windows 11, but is quite similar on Windows servers as well.

Upon enabling WEBDAV, the next step is to create a virtual directory under our root website. In this instance, we’ll name it webdavshare and mount it, for the sake of simplicity, on the C:\Windows directory.
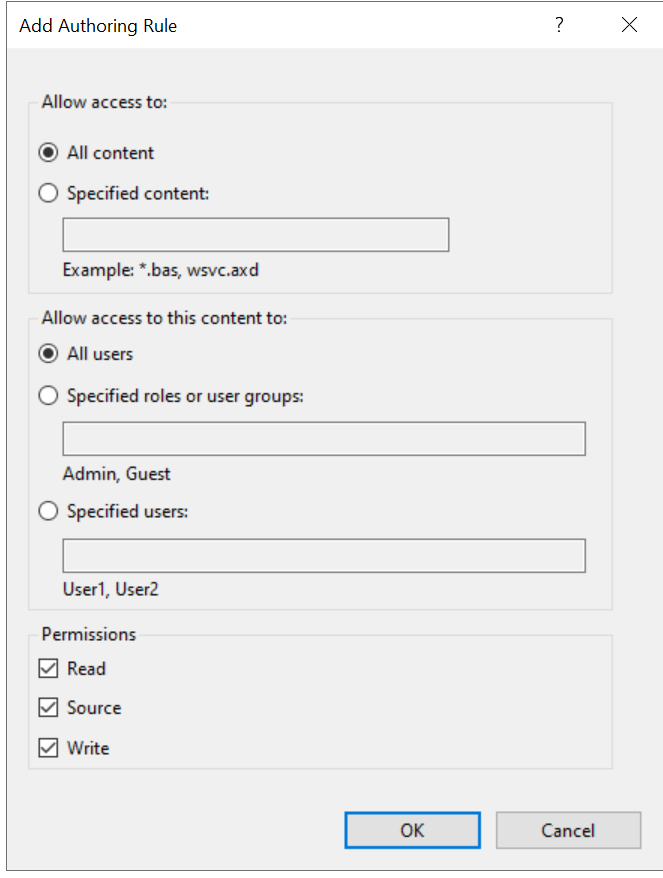
We need to permit read/write operations on this share by adding an authoring rule:
Last but not least, we need to enable NTLM authentication and disable all the other methods:

Exploiting context swapping with http/webdav
In our latest LocalPotato release, we have added and “hardcoded” this method with http/webdav protocol. The tool will perform an arbitrary file write with SYSTEM privileges in the location specified in the webdav share with a static content of “we always love potatoes”. Refer to the source code for all the details, it’s not black magic 🙂
You can certainly modify the code and tailor it to your specific needs, depending on the situation you encounter 😉